Goodmorning and have a nice week everybody! The other day, I posted the results of our latest research. This research was all about “Microsoft-Windows-Partition%4Diagnostic.evtx”, an Event Log found in Windows 10 (Read our research here). During this research, a member of our team, Dimitrios, developed a quick-win tool (written in Python) to parse the above-mentioned Event Log file. Today, he is sharing with us a walkthrough of how to use his newly developed tool (Tool is available for download here). Enjoy.
Introduction
Partition%4DiagnosticParser is a Python tool that parses the Windows 10 Microsoft-Windows-Partition%4Diagnostic.evtx event log file (located in C:\Windows\System32\winevt\Logs) and reports information about all the connected devices and their Volume Serial Numbers, both currently present on the device and previously existed. It accomplices this task by doing the following:
- parsing all the records in the event log,
- analyzing the “Vbr” elements of each record (so as to translate them into meaningful Volume Serial Numbers) and
- attribute interpreted VSNs to the specific connected device they belong to.
When you launch Partition%4DiagnosticParser, you will see the following window:
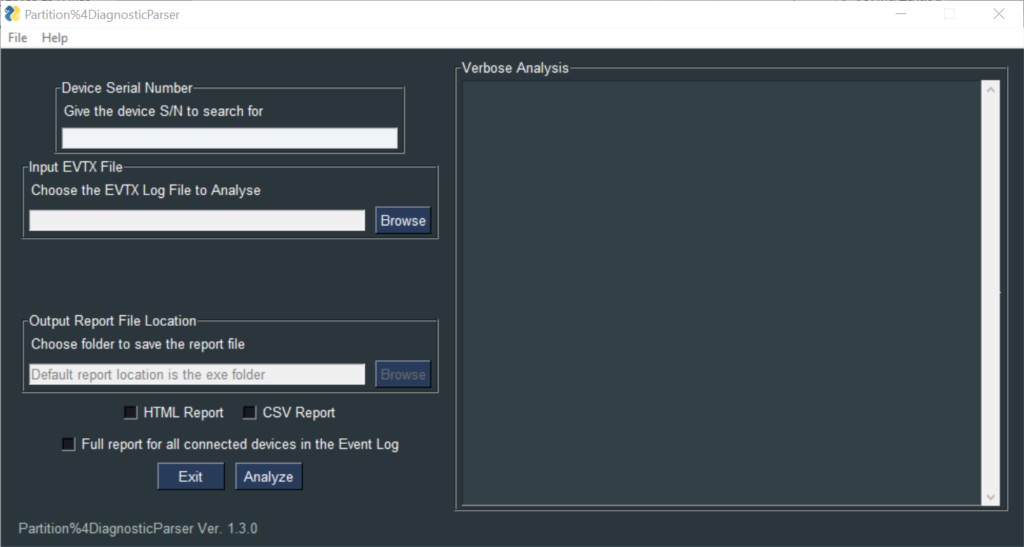
As you may see, the tool provides two main functionalities:
- Full Report
- Targeted S/N analysis
We shall see how to use each one of them.
Full Report
- User provides the tool with the “Microsoft-Windows-Partition%4Diagnostic.evtx” event log file to analyze (via the browse button in the “Input EVTX File” field). The input file can be either an exported event log from a forensic image file or from a mounted disk image (Dead Box Forensics). It can also be a “copy” of the event log file of a live system (copy is needed so it can be parsed successfully).
- User checks the “Full report for all connected devices in the Event Log” checkbox.
- User chooses an output folder to save the HTML report which will be created (if left blank the default output folder is the current directory in which the Partition%4DiagnosticParser is being executed from).
- User presses the “Analyze” button.
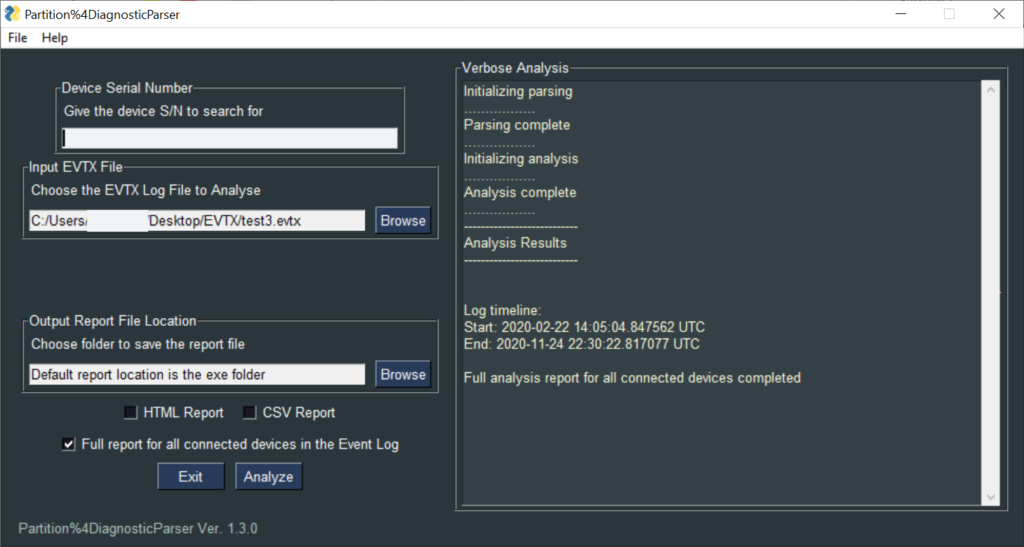
The verbose analysis pane informs the user about the successful completion of the analysis and provides the timestamps for the time span that is being covered by the log file.
Full Report – HTML Report
The HTML report created after the analysis, display all the devices that have been connected in the computer and thus logged in the event log (number of devices is analog to the lifespan of the log). For each device the tool provides:
- Its serial number (S/N),
- The manufacturer – model,
- First and last timestamp the device was connected in the computer and
- The Volume Serial Numbers that existed on the device historically throughout the whole log. This means VSNs from currently existing Volumes on the device, along with the previously existed ones.
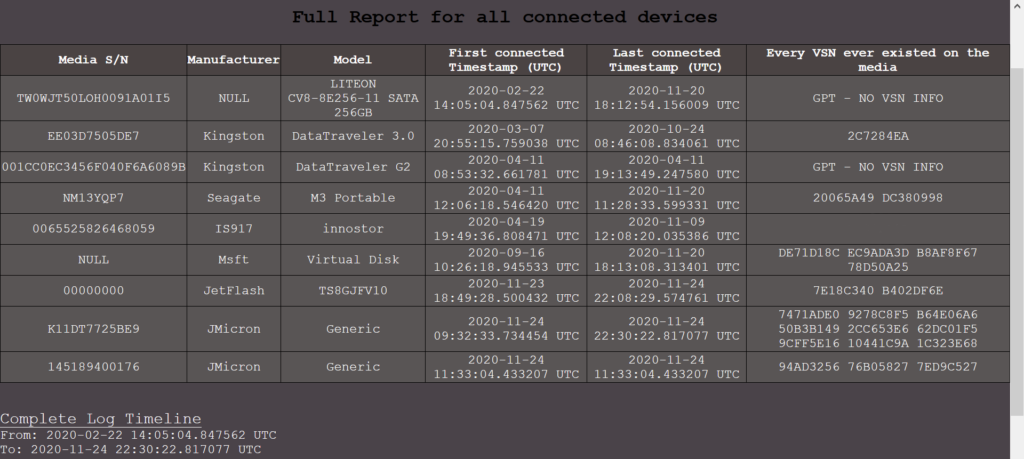
Full Report – Key points to consider when interpreting the results of the analysis
- Due to the nature and structure of the event log, VSN information is available only for the first three (3) Volumes of a device. This means that a possible 4th partition existing on the device can be missed from the analysis and results.
- A result of “GPT – NO VSN INFO” on the VSN column, indicates that the device has been formatted with a GPT partitioning scheme and thus no available information can be provided about its volumes.
- A completely empty result on the VSN column, indicates that the device had volumes formatted with non-Windows File Systems throughout the whole log’s lifetime and thus no available information can be provided about its volumes, regardless of the device’s Partitioning Scheme.
- Given that the log can provide info about the first 3 Volumes formatted with Windows File Systems, any result containing more than 3 VSNs on the VSN column, indicates that the device has been formatted at some time during the log’s lifetime and its VSNs have been changed. This pinpoints a device of interest that can be examined more thoroughly with a further Targeted S/N analysis.
Targeted S/N analysis
- User provides the serial number of the device of interest (at the “Device Serial Number” field).
- User provides the tool with the “Microsoft-Windows-Partition%4Diagnostic.evtx” event log file to analyze (via the browse button in the “Input EVTX File” field). The input file can be either an exported event log from a forensic image file or from a mounted disk image (Dead Box Forensics). It can also be a “copy” of the event log file of a live system (copy is needed so it can be parsed successfully).
- User checks the “HTML Report” or “CSV Report” checkbox (or both), depending on his needs.
- User chooses an output folder to save the HTML report which will be created (if left blank the default output folder is the current directory in which the Partition%4DiagnosticParser is being executed from).
- User presses the “Analyze” button.
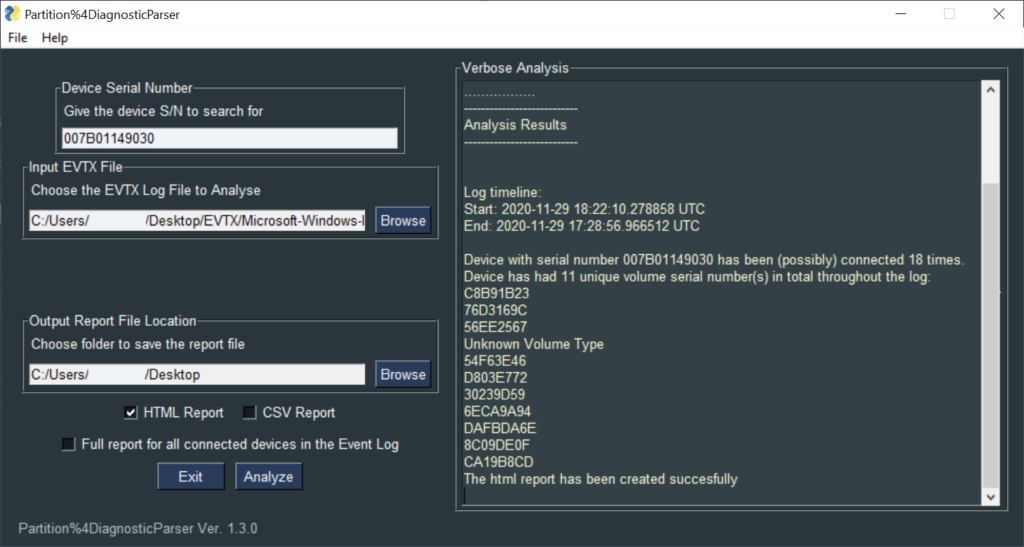
The verbose analysis pane informs the user about the successful completion of the analysis and provides the timestamps for the time span that is being covered by the log file. It also provides the unique VSNs that the device had in total throughout the log’s lifetime.
WARNING: Due to the logging behavior of the event log, the verbose analysis pane cannot provide the accurate number of times the device had been connected in the computer. For example, if a format action of a device is taking place on the same computer (to which the event log belong to), the event log will add a new entry that resembles in every way a plug-in action (whereas the device was never unplugged from the computer). Therefore, the verbose analysis will give a rough estimation about the total number of times that the device has been connected to the computer (this is why the word “possibly” is used in the result).
Targeted S/N analysis – HTML Report
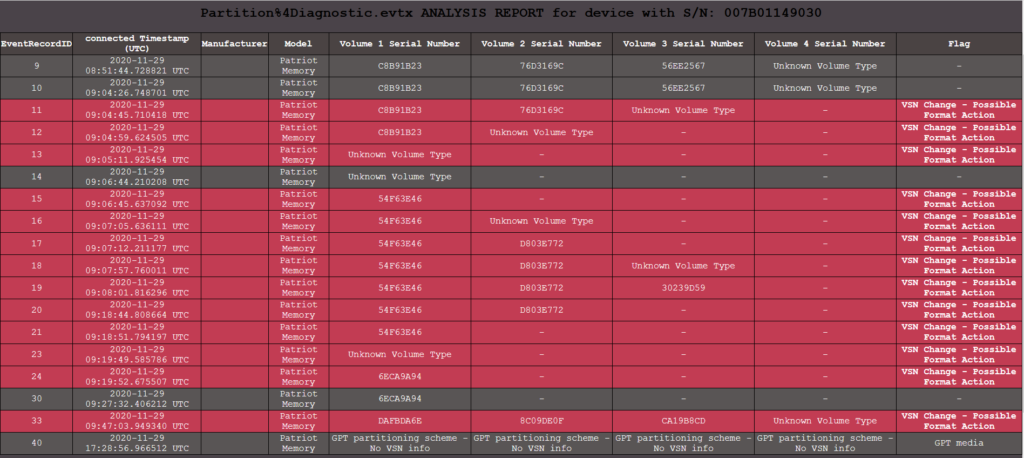
The HTML report created after the analysis, provides an actual timeline of all the times the device was connected to the computer and thus logged in the event log (number of connections is analog to the lifespan of the log). For each connection the tool provides:
- The Record Event ID for the examiner to crosscheck the info with the actual event log,
- The timestamp the device was connected in the computer (in UTC),
- The manufacturer – model,
- The Volume Serial Numbers that existed on the device during the timestamp of that particular connection and
- A Flag interpreting the current state of the device with regard to the previous time it was connected to the computer (providing a message when a VSN change is detected, indicating that a format action may have occurred – the html row will be highlighted in that case).
Targeted S/N analysis – Key points to consider when interpreting the results of the analysis
- A result of “–” in any Volume Serial Number column, indicates that there was no existing Volume on the device at the time of the connection.
- A result of “Unknown Volume Type” in any of the first 3 Volume Serial Number columns, indicates that there was a Volume on the device at the time of the connection that was formatted with a non-Windows File System. This can also mean that the Volume was being deleted as a part of a format action taking place on the same computer by the user as will be explained later on this section.
- A result of “Unknown Volume Type” in the 4th Volume Serial Number column, simply indicates the existence of a 4th Volume. Due to the logging behavior of the event log(4th Volume’s VBR never gets logged on the log file), no safe results can be extracted for the 4th Volume. What is more, the “Volume 4 Serial Number” column will never provide the user with an actual VSN. Nonetheless, the existence of an “Unknown Volume Type” record entry, indicates that the device did indeed have a 4th Volume at that time (Present with a non-Windows File System or deleted during a format action). This value is different from “–” which means that the device had no 4th Volume at the time, whatsoever.
- A result of “GPT – NO VSN INFO” on all the Volume Serial Number columns, indicates that the device was formatted with a GPT partitioning scheme at the time of the connection and thus no available information can be provided about either its volumes, or the total number of them and their respective Volume Serial Numbers.
- The highlighted row and the existence of the warning Flag “VSN Change – Possible Format Action” occurs when the device has any of its 4 Volume Serial Numbers changed in comparison to the exact previous time it was connected to the computer. In such cases, the investigator can also conclude whether the format action took place in the computer under investigation (when entries are being logged successively with a few seconds difference between their timestamps). This means, that the user consecutively deleted one by one the existing volumes and created new one/ones. In every Volume deletion happening on the computer, the event log will add a new entry, whose VBR of the deleted volume consists of a series of 512 zeroes. In those cases, the tool will provide a result of “Unknown Volume Type”.
In this post, Dimitrios explained all the necessary information someone might need, in order to successfully use Partition%4DiagnosticParser and properly interpret its results. I am really thankful to him for this great tool he provided us with. I am pretty sure you will love this tool too, especially when you will need to extract all the VSNs there are in the above-mentioned log. If you haven’t yet tried it, you will find it here. If you found this post useful, do not forget to share it. See you next time.

